Step 6: Rate and assess cyber security risks
The rating of cyber security risks involves two critical components: Business Impact and Likelihood.
Business impact is a measure of the harm a cyber incident could inflict on the organisation's operations, assets, reputation, or financials. It involves understanding both tangible consequences, such as financial loss and legal liabilities, and intangible consequences, such as reputational damage and customer trust erosion.
Recognising actual business impacts is crucial, as it enables prioritisation based on the severity of consequences, ensuring resources are allocated where they are most needed.
For instance a website denial of service will have different business impacts dependent on the website’s function and value. Disruption to a website which is used as an e-commerce sales channel will have a much higher business impact than disruption to an annual leave booking website for staff at the same business. The technical impact is identical, but the business impact is radically different.
Likelihood is a measure of the probability of a specific cyber incident occurring. This considers factors like historical data, threat intelligence, and security controls in place. It gauges the chances of an event occurring, from highly unlikely to almost certain. Understanding likelihood allows for targeted risk mitigation efforts, focusing on scenarios with higher probabilities of occurrence.
Important to understand is that likelihood can vary over time. For instance a shift in the threat landscape can increase likelihood of a cyber incident occurring. A good example of this is the increase in ransomware threat over the past 5 years. Arguably this has increased the likelihood of cyber incidents across the board, for businesses large and small. The increase in sovereign state threat as a result of the Ukraine war is another example of this.
An example of increased likelihood due to insufficient security controls could be seen in a SaaS service where user accounts are not protected by MFA.
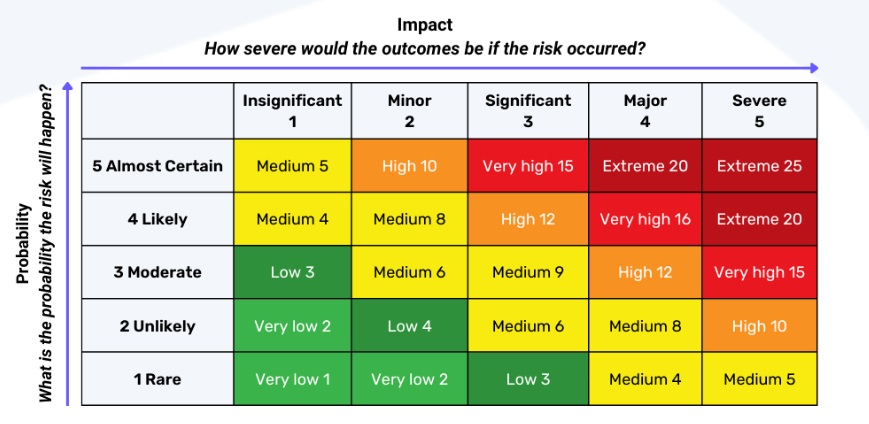
Once an understanding of business impact and incident likelihood has been built a cyber security risk assessment matrix is used to factor these two variables together and deliver a cyber security risk assessment, such that that overall risk rating is a consideration of both variables. This matrix rates risks based on their likelihood and potential impact, typically on a scale of low to high or critical. By plotting risks on this matrix, organisations can simply and comparatively rate risks.